“Be proactive, not reactive, for an apparently insignificant issue ignored today can spawn tomorrow’s catastrophe.” ~ Author Ken Poirot
Though Mr. Poirot most likely wasn’t speaking of vulnerability scanning or penetration testing, his quote perfectly sums up their essence. Vulnerability scanning and penetration testing are two proactive cybersecurity defenses organizations can use to assume a preventative posture for their cybersecurity. These two methods help reveal weaknesses throughout digital infrastructures, software, and even human-related security risks.
Firewalls, anti-virus software, and password-protected access are vital cybersecurity tactics. But what if your firewalls are overburdened, or your anti-virus software is out of date, or weak passwords reside over your sensitive data? What if an application is missing the latest security patch? Would you know if your network is misconfigured? Would you take a reactive stance and wait till a cybercriminal breaches your data to fix these issues—or get ahead of hackers with vulnerability scans and penetration tests?
What Is Vulnerability Scanning?
 Vulnerability scanning—sometimes called vulnerability assessment or analysis—is a method to discover and remediate vulnerabilities within an organization’s networks, operating systems, and processes. Once a scan unveils weaknesses, then the associated components and root cause must be identified. The vulnerabilities can then be triaged in order of severity for a solutions plan.
Vulnerability scanning—sometimes called vulnerability assessment or analysis—is a method to discover and remediate vulnerabilities within an organization’s networks, operating systems, and processes. Once a scan unveils weaknesses, then the associated components and root cause must be identified. The vulnerabilities can then be triaged in order of severity for a solutions plan.
What Kinds of Vulnerabilities Can a Scan Detect?
Comprehensive automated vulnerability scans can reveal weaknesses in an organization’s hardware, software, and systems, and even human-induced failings, such as weak passwords.
- Software bugs
- Old or missing security patches
- Configuration errors
- Out-of-date virus software
- Overloaded firewalls
- Unsecure email services
- Users Errors
- Weak passwords
What Other Factors Can a Vulnerability Scan Expose?
- The system that is affected
- Business functions associated with the affected system
- What data is stored in the system
- The age of the vulnerability
- Regulatory requirements for your organization, such as HIPAA
Why is Vulnerability Scanning So Critical?
 Leaving weaknesses—such as configuration errors or software bugs—unchecked threatens basic business continuity and productivity. Your compliance could also be at risk if your system doesn’t meet regulatory requirements or presents security risks to related data. But perhaps the most significant threats are the vulnerabilities that cybercriminals can exploit to infiltrate your system and access valuable data. Vulnerability scans unveil these potential disruptions and criminal ingresses, saving you valuable time, money, and other losses from regulatory consequences.
Leaving weaknesses—such as configuration errors or software bugs—unchecked threatens basic business continuity and productivity. Your compliance could also be at risk if your system doesn’t meet regulatory requirements or presents security risks to related data. But perhaps the most significant threats are the vulnerabilities that cybercriminals can exploit to infiltrate your system and access valuable data. Vulnerability scans unveil these potential disruptions and criminal ingresses, saving you valuable time, money, and other losses from regulatory consequences.
How Often Should a Business Perform a Vulnerability Scan?
Many industry experts suggest conducting vulnerability scans at least once a year. But a lot can happen in a year. Organizations may change or update their business processes or computer hardware, and mutable APIs, web applications, software, code, and software populate their digital infrastructure. Changes—both intentional and accidental—can occur that could spawn continuity and security threats. More frequent automated scans can keep businesses abreast of their vulnerabilities and ahead of hackers, helping to prevent disruptions and data breaches that unknown flaws can trigger.
Vulnerability scans are a crucial element of risk management, but businesses can take their proactive security to the next level with penetration testing.
Penetration Testing
Typically, organizations perform penetration tests—or pen tests—after conducting vulnerability scans to reveal weaknesses. This proactive probe replicates a cyberattack on an organization’s computer systems to determine if a bad actor could exploit known vulnerabilities and breach a network or access sensitive data. Not only can pen tests reconnoiter an organization’s networks and application configurations, they can also scrutinize employees’ actions that could precipitate data breaches.
How Does Pen Testing Differ from Vulnerability Scanning?
Vulnerability scans discover weaknesses. Pen tests will determine the threat level of those weaknesses. For instance, you may discover a weakness that appears to harbor high-risk potential, but a pen test reveals that the exploitation would be challenging to execute. Pen tests can also enhance a company’s incident response competency—the more practice a business acquires with simulated attacks, the better equipped it is to respond to a real-life breach.
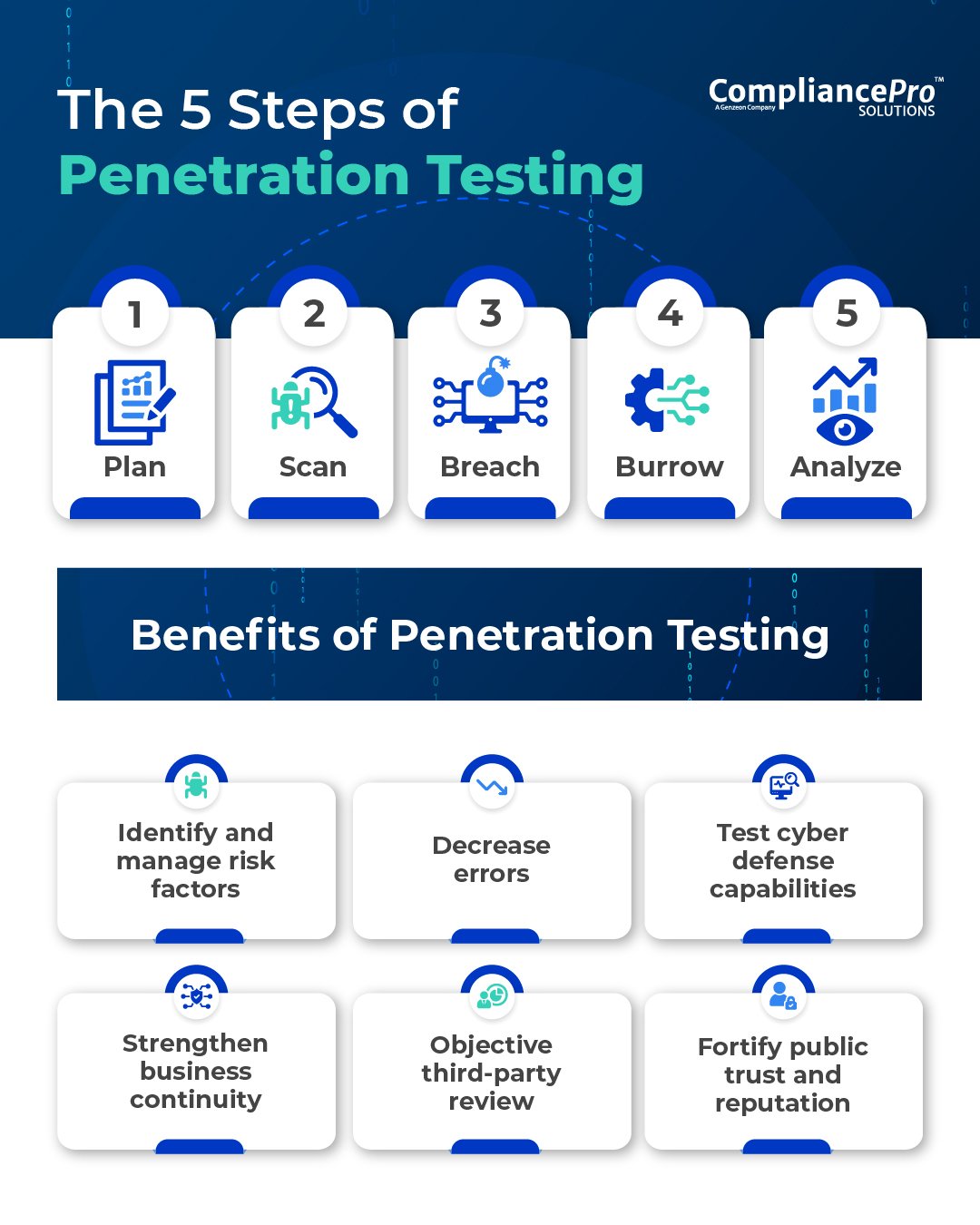
Benefits of Penetration Testing
- Identify and manage risk factors
- Decrease errors
- Test cyber defense capabilities
- Strengthen business continuity
- Objective third-party review
- Fortify public trust and reputation
The 5 Steps of Penetration Testing
Cybersecurity professionals typically perform comprehensive pen tests in five stages:
- Plan
- Scan
- Breach
- Burrow
- Analyze
1- Plan
In this first stage, a pen tester establishes test goals and gathers relevant data.
2- Scan
Next, the tester uses various tools to learn how a system responds to assorted attacks.
3- Breach
This is where the tester moves in for the attack using SQL injection, cross-site scripting, or backdoors to exploit vulnerabilities and breach the organization’s system and data.
4 - Burrow
Here, the pen tester ascertains how much farther he can ferret into the system and for how long. This will help determine if an attacker can maintain a persistent presence to steal data.
5 - Analyze
The results of a pen test can then be detailed in a report and assessed to draw remediation strategies.
When Should You Perform a Pen Test?
A thorough penetration test should be conducted annually or when you:
- Add a new network
- Install new software
- Relocate your office
- Set up a new end-user program
- Discover new threats
- Conduct vulnerability scans that reveal new issues
Is Your Data Security Worth the Cost of a Breach?
Organizations may feel penetration testing is too time-consuming and costly—particularly for small organizations with small budgets and limited resources. But when you consider that the average global cost for a data breach in 2022 was $4.3 million, pen testing might be worth a place in the budget.
A Dynamic Duo of Defense
Vulnerability scanning is only one small piece of armor in a company’s security defense, but it is a vital one. Combined with penetration testing, the two can forge powerful proactive protection.
For more information about vulnerability scanning and penetration testing, visit CompliancePro Solutions.