9 Ways to Spot a Phishing Attack at a Glance
Phishing attacks cause more than 90 percent of all data breaches. Prevention is the best way to avoided becoming a phishing victim—and prevention means knowing what to look for and recognizing fraudulent text, emails, social media activity, and phone calls.
Learn how to spot a phishing attack before it’s too late.
- Typos and Poor Grammar
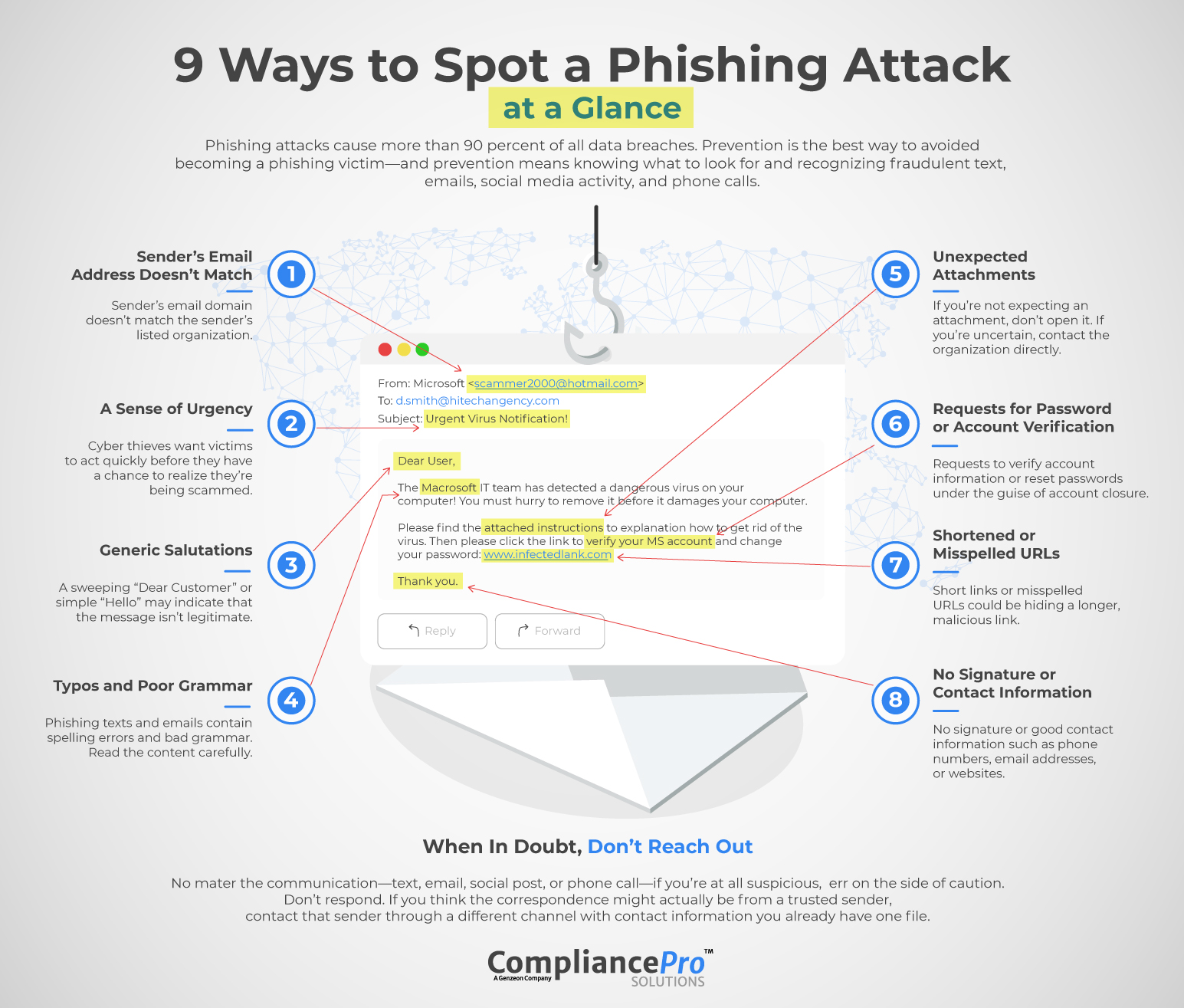
Often, phishing texts and emails contain spelling errors and bad grammar. Read the content carefully. However, this may not be as reliable if attackers use AI to write the communication. - A Sense of Urgency
Cyber thieves want victims to act quickly before they have a chance to realize they’re being scammed. They may tell you your computer is infected with a virus or threaten you with jail time or hefty fines for something such as legal issues or unpaid taxes. - Generic Salutations
Most legitimate senders now use a recipient’s name. A sweeping “Dear Customer” or simple “Hello” may indicate that the message isn’t legitimate. But spear phishers do get personal, so always look for other clues of fraud. - Sender’s Email Address Doesn’t Match
A good way to identify a bogus email is if the sender’s email domain doesn’t match the sender’s supposed organization. Example: The email looks as if it’s from Verizon, but the sender’s email is “gotcha@gmail.com.” Professional organizations never use free email domains. - No Signature Contact Information
Fictitious emails often don’t contain good contact information such as phone numbers, email addresses, or websites, as legitimate emails would. - Requests for Password or Account Verification
Any request to verify account information or reset passwords under the guise account closure or if a very common tactic. - Unexpected Attachments
If you’re not expecting an attachment, don’t open it. If you’re uncertain, contact the organization directly—but don’t use any contact info within he suspicious communication. - Caller Refuses to Give Return Phone Number
If you’ve received a suspicious phone call asking for personal information, first ask the caller for a return number so you may verify the legitimacy. If the caller refuses, hang up immediately. - Shortened or Misspelled URLs
Short links could be hiding a longer, malicious link. Also, a misspelled URL is a good indicator of fraud. Always hover your mouse over links before clicking.
READ: Get Smart About Cybersecurity - Security White Paper
When In Doubt, Don’t Reach Out
No mater the communication—text, email, social post, or phone call—if you’re at all suspicious, err on the side of caution. Don’t respond. If you think the correspondence might actually be from a trusted sender, contact that sender through a different channel with contact information you already have one file.